Empower Secure Collaboration with Incident-Level Permission Management
While anyone at your organization should be able to start Blameless incidents, not everyone should have access to all current and past incidents (nor retrospectives), particularly when those incidents are handling sensitive and confidential information related to security issues. With Blameless you can already restrict the creation of incidents and access to incidents (and retrospectives) on a per incident type basis. Now, you can also allow Blameless users only to access the incidents (and their corresponding retrospectives) that they create, while preventing access to all other incidents of the same incident type. Additionally, at any time during or after the incident, if deemed necessary for security or confidentiality reasons, users who created the incident or joined the incident, can have their permissions to access the incident easily revoked. Meanwhile, users joining incidents without any pre-assigned Blameless identity roles, can be granted more permissions (Reader, Writer) to access and interact with the Blameless incident (and retrospective).
Assign the new IncidentCreator role to users
Restricting incident creators to create and access only incidents they created in Blameless is pretty easy. Under Identity Management in Blameless, a Blameless administrator with the IdentityAdmin permission, just needs to assign the new IncidentRole to users via a group, which is automatically created by default per incident type, along with the IncidentReader, IncidentWriter and IncidentAdmin roles (see incident roles).
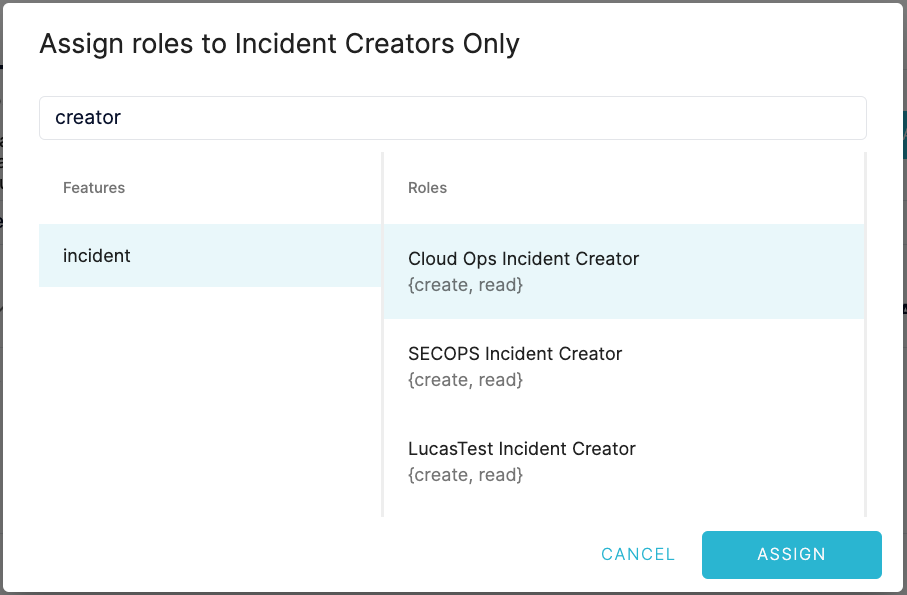
Users who have been granted the IncidentCreator role for a specific incident type are automatically invited to the incident they created and are granted permissions to execute a limited set of commands corresponding to the IncidentReader role (see incident roles), but only for incidents they created. Additionally, they can only access the incidents and retrospectives they have created via the Blameless incident. Other incidents (and retrospectives) will not be accessible to users who have only been granted the IncidentCreator role.
Additionally, users who have been granted the IncidentCreator role gain Reader permissions to the incident they created, which provides access to the same Blameless commands that the IncidentReader has access to today (see incident roles).
Note that you should make sure that users with the IncidentCreator role, are also not assigned one of the other default incident roles such as the IncidentReader, IncidentWriter or IncidentAdmin for a selected incident type, otherwise it would override the restricted permissions set by the IncidentCreator role, still granting them access to all incidents of the same type.
Updating permissions during the incident
Conditions may change after incidents have started, so Blameless provides the flexibility to grant more Blameless permissions to users as they join incidents or to revoke permissions to access the Blameless incident (and retrospective) if the incident has to be handled and accessed only by a reduced number of authorized users.
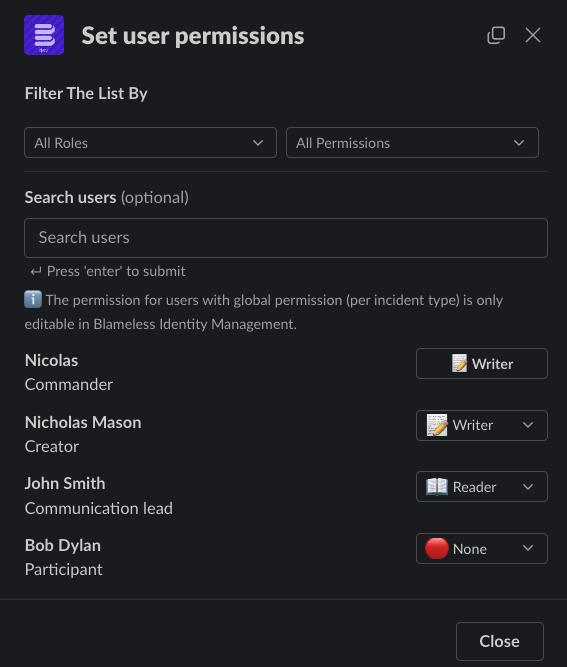
You can view and change user permissions (grant/revoke) at the incident level only (local roles) without leaving the incident channel in Slack using the new /blameless set permission command or from the incident detailed page in the Blameless web UI. For security reasons, note that only users with the IncidentWriter role for this incident type have permission to change the local user permissions.
View permissions
You can view the user permissions (local and global roles) for any users joining the incident, including the creator of the incident and anyone who joins the incident.
- Users joining an incident may have permissions set either at the incident-level only (local) or at the global level per incident type (or all incident types)
- Note that if a user has a role set at both the global and local level, the permissions at the global level prevail.
Changing permissions
You can change permissions for users with local roles only. Permissions inherited at the global level (per incident type) can only be updated under Identity Management in Blameless.
Call to action
To benefit from this new role-based access control (RBAC) enhancement (permission per incident), contact your Blameless administrator responsible for managing user access in Blameless under the Identity Management section, to start granting users with the permission to access only the incident (and retrospective) they create. Check the instructions on how to configure and change permission per incident here: https://docs.blameless.com/hc/en-us/articles/22773768650007-Permissions-per-incident

.svg)